-
Notifications
You must be signed in to change notification settings - Fork 17
Referrer leakage at a certain website #78
Comments
|
|
|
I could not reproduce with Chromium 70/Linux on my side. This reminds me of this issue: #74 -- though not confirmed by OP, it appears the |
|
I can reproduce on Chromium 70.0.3538.67/Windows on my end. |
|
Ok I could reproduce, I had to allow some 3rd-party scripts in the matrix. After investigating, I confirm uMatrix really removes the However, the browser still sets the |
my bad, forgot to add you need to whitelist
but this website only ? Other referrer testing websites work fine. Is the website triggering some exploit ? |
|
Speaking of |
|
There are two ways a site can report to you the referrer they see: server-side or client-side. If server-side, the referrer is looked up from the request headers, hence it will be spoofed. If client-side (requires javascript code to be executed), the referrer will be looked up from |
|
Guessing they're picking the client-side value right ? |
|
Yes, load https://www.myip.com/js/graf.js and scrolled to the end. |
|
I consider this a browser bug, this is what needs to be fixed. No reliable workaround can be crafted to match current referrer-spoofing feature -- at best, a workaround would be unreliable, i.e. easily bypassed by having script code executed at the top of a document, before uMatrix's own content script can patch the referrer according to current ruleset. I rather there be a real, actual fix than the appearance of one. My official suggestion would be to just use Firefox if rock-solid referrer spoofing is important. |
|
No I'm fine, thought I would suggest one until |
Can't find any bugs filed on the tracker. Do you know of any ? |
|
Keep it open, I remembered there is this new |
I looked into this, and I found that ScriptSafe adds a |
|
Is there any extension of Referrer Policy ? I want to see it in action once and see it deals. |
|
Made a uBO-Scriptlet to patch |
|
The extension Referer Control at https://chrome.google.com/webstore/detail/referer-control/hnkcfpcejkafcihlgbojoidoihckciin?hl=en is blocking the referer with success on 3rd party requests. |
|
Yes, like this -- |
|
@uBlock-user could you made this part from your uBO-Scriptlet? |
|
It's better if the fix lands in the extension itself, rather than having to use a scriptlet in ublock. |
|
I agreed. I tried to play with the options in this Referer Control extension... I tested of few pages with which I had referer leakage with uMatrix before and seems to work well. I am not sure if that can be implemented in uMatrix. |
|
referrer-spoof not work in Chrome 72+, working on Chrome 71 now |
|
@HashLiver Probably related to #74, fixed in dev build. |
|
The extension Privacy Manager is working really well about hiding the referer in Chrome. The uMatrix is not working of some pages. The referer control extension is working on every site tested but I had cases in which I had to disable the blocking the referrer string of third-party requests in order the page to work properly. I don't know how they do but surprisingly, the Privacy Manager is working on every page tested. |
This comment has been minimized.
This comment has been minimized.
|
@uBlock-user did you ever get this working on chrome? I have been trying a number of techniques to get around this to no avail. |


Prerequisites
Description
Referrer leaks at
https://www.myip.com/when visited via google search result.A specific URL where the issue occurs
https://www.myip.com/Steps to Reproduce
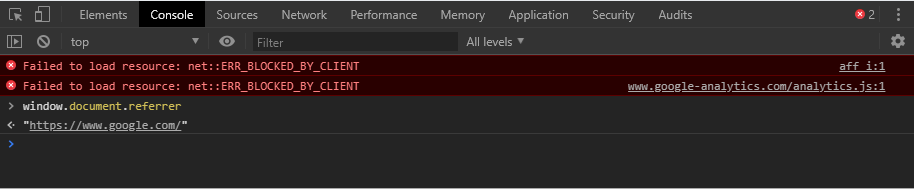
https://www.google.com/https://www.myip.com/and scroll down to the end of the page to locate Referrer field showingURL: www.google.comSupporting evidence
Logger shows that REFERRER was blocked yet the website is able to detect.
Your environment
The text was updated successfully, but these errors were encountered: